Techsplained: How can you protect yourself from Ransomware Attacks?
If you enjoyed this video we have many more on our YouTube Channel to help you improve your tech knowledge, give you advice and even “How To” videos.
If your business is hit with a Ransomware Attack you could lose more than just your files.
Techsplained, uncomplicating technology and making it easy for you.
In this video and article we are going to discuss Ransomware in more detail.
What is Ransomware? How serious could it be for you and your business if just one of your computers becomes infected with Ransomware?
If you find that one of your computer has become infected with Ransomwarewhat should you do? And how quickly can Ransomware spread to other computers on your network?
And how can you protect yourself from Ransomware attacks?
We will cover all this and more in this video and our below article.
What is Ransomware?
Ransomware is a name given to a type of virus or piece of malware that can infect your computer or network. Once infected, the ransomware could spread to all of the files on your system and lock, or encrypt them. If this happens, you may not be able to access any of your files, and when you do try you may be presented with a file that did not originate from your computer, this could be an image or text file, or you may be presented with some form of a ransom screen. [show wannacry screenshot]
In the majority of cases the attacker will demand a sum of money in BitCoin or some other form of cryptocurrency in exchange for the key to decrypt your files.
However, it is also worth noting that in the UK, data regulation laws mean you can also face fines if personal data is stolen as part of a data breach from a ransomware attack or other hack/data breach.
How serious are Ransomware attacks?
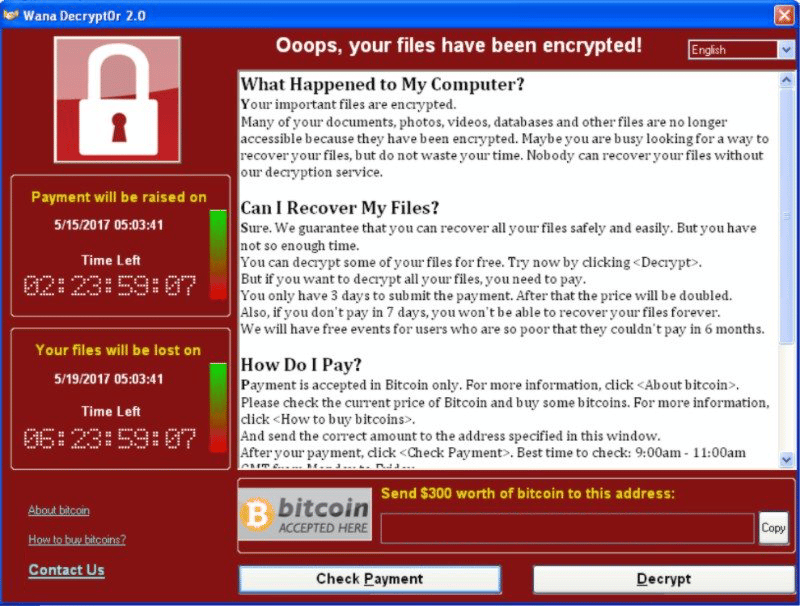
At One2Call we regularly hear about businesses who are not covered by any form of ransomware protection being targeted in these types of attacks. In the US it is estimated that ransomware attacks against businesses occur roughly every 11 seconds with businesses asked to pay on average more than 200 thousand dollars per attack.
And for those people and businesses who choose not to pay, and are not protected, it can take anything up to 20 days to recover from an attack and in many cases businesses will still have lost many, if not all, of their files, not to mention any loss of business and earnings as a result. Just think if your business could not operate properly for up to 20 days, how much money would you lose?
Aven major companies are not immune to ransomware attacks. In the UK, in 2017, the NHS was targeted by the WannaCry Ransomware virus, more than 40 NHS Trusts and Hospitals were unable to serve patients, load records, give x-rays or process bloodwork. On top of this, thousands of NHS patient records were stolen. Analysts have estimated that the NHS lost more than 90 million pounds in the attack.
It is estimated that the total global loss caused by the WannaCry ransomware virus to date is in the range of 4 billion US dollars.
How can you become infected by a Ransomware attack?
In many cases Ransomware attacks are the result some form of Phishing attack, you can learn more about Phishing attacks, how you can spot them and how to prevent against them at this link.
These phishing attacks may include a link to steal your log in credentials, to access your computer, network or download a malicious file to your system that starts the attack. Attacks could even come from a malicious advert on a website that you click on, which downloads a file to your computer when you click on them.
Once the virus starts to infect your computer and network it can quickly bring you or your business to a grinding halt. Recently, Colonial Pipeline in the US suffered a severe cyber attack which caused the firm to shut down it’s fuel distribution network. Causing fuel shortages across many states in the southern US. In this instance attackers launched the Ransomware attack by gaining access to a VPN account for a user who’s user details had previously been exposed in a data breach on the dark web. This account was out dated and no longer actively in use by anyone in the business. The credentials for the account had not been removed, disabled or the password altered, and no Two Factor Authentication was required. Due to this, the attackers were easily able to use information found on the dark web to access the Colonial Pipeline systems.
The attackers reportedly accessed and explored the Colonial Pipeline systems for more than a week before activating the ransomware and sending the ransom note. Colonial Pipeline paid more than 4.4 million dollars to end the cyber attack, and they probably lost more than that in lost business. If Colonial Pipeline had active Dark Web Monitoring, this attack could have been prevented, as they would have been notified about the vulnerable account before the attack occurred and they could have ensured that these credentials were no longer valid on any of their systems.
If you want to find out more about One2Call’s Active Dark Web Monitoring service click on the link below. On that page you can also request for a FREE one off dark web scan for your business.
Does Ransomware just infect one computer?
Ransomware can quickly effect any and all files that you can access. These may be just be those located on your computer. However, if you have access to shared network folders this can mean that these files can also become infected. It doesn’t just stop there though as if one file on your network becomes infected then it could potentially spread to other files that you may not have access to. Before you are even aware of it, all of your businesses files could be locked and encrypted.
As we saw in the Colonial Pipeline Ransomware attack, one vulnerable user account was all it took to launch a ransomware attack which cost the company millions of dollars.
What should you do if you are infected from Ransomware?
Isolation
If the worst does happen and you discover that one of your users is infected as the result of a ransomware attack it is important to Locate and Isolate every infected user and device as soon as possible. To do this it is best to remove every device from your network as soon as you can, especially those which already appear to be infected, you can do this by disconnecting their Cable network connection or their WiFi network connection.
If you can find the source of the infection they could also be used to hopefully trace who else may be infected. Next it is important to isolate all potentially infected drives, these could be USB drives, hard drives, network drives or even potentially server storage.
Once this has been done you can run security scans on all of your other machines to ensure that they are not at all infected. It is also important to also evaluate all of your backups and cloud storage to ensure that none of these were also infected.
Once this has been completed you should arrange for all of your infected machines to be isolated from all network activities to ensure that no files or folders can be shared with each other, or any cloud storage service. Once you have done this you can reconnect these to the internet, just be sure that they can not access the rest of your network and they only have a direct route out to the internet, at that time you can then attempt to use tools such as No More Ransom to attempt to unlock your files. This is not guaranteed to work though.
If this does not work, and you have evaluated your backups to ensure that these are not infected, you should restore your machines back to factory state and restore your backups to a clean version which is not infected by the ransomware.
What should you be doing to mitigate the risks of Ransomware Attacks?
Whilst Ransomware can cost you or your business a lot of money or leave your business crippled as the result of an attack, you may be surprised that protecting yourself from Ransomware attacks is easy and in the grand scheme, quite inexpensive. When protecting yourself there are few things that you need to consider;
Updates
Does your computer have all of the latest software updates and security patches installed on it?
Security updates are released on a regular basis for all major providers to help your protect from potential vulnerabilities from the latest threats. It is good practice to check for these updates on a regular basis. At One2Call our Managed IT Support can notify us if any computer updates are waiting to be installed and force an update schedule to them if they are not done after a certain amount of time.
Security
When installing software, it is important that you do not give admin permissions to the software unless you understand exactly what it does, what it can access and if it is from a verified and reputable source.
Anti-Virus / Endpoint Protection
Do you have a suitable Anti-Virus that is actively updated to protect you from the latest viruses as soon as they are found and a protection from them developed? Our Anti-Virus solution connects to a database which is updated live 24 hours a day, every day of the year with all of the latest threat prevention tools to ensure you are protected against the latest known viruses as soon as possible.
Email Security
The majority of ransomware attacks originate from phishing attacks or emails. As such, one of the best ways to protect yourself from ransomware attacks such as these, are from the source, by preventing phishing emails and malicious links being received in the first place. This is where Active AI Powered Email Threat Prevention comes in.
At One2Call, we can offer real time mailbox scanning and monitoring to ensure you are protected from receiving phishing emails; It can verify links you receive in emails to ensure that they are legitimate & it can identify potentially vulnerable people in your business who are at risk from attacks such as Managers, Directors and Financial staff members.
If you want to find out more about our Active AI Powered Email Threat Prevention click on the link below. You can also request for a FREE one off mailbox security scan to check for vulnerabilities in your businesses emails.
Backups
Another thing that you should be considering is your backup process. Do you have adequate backups of all of your files?
Do you know what the 3,2,1 backup method is? Backups are an essential part of a businesses IT strategy. The 3,2,1 backup strategy says you should always have 3 copies of your files, one on your computer/primary storage medium, one backed up externally, on your network on another form of external storage. And a third, remote backup, that is in a different building to your first and second copy of your files, ideally on a separate network entirely. If your files are backed up like this then you can ensure that you will always have a copy to restore from if the worst does happen.
How can you protect yourself from Ransomware Attacks?
The first question you should be asking yourself though is, are you protected with financially backed ransomware protection that can monitor your files for all known forms of ransomware, and that is updated regularly as soon as new variations are detected and decrypted? If you are at all concerned about you or your business being exposed to ransomware and you’re not covered by all of the things we have mentioned then we advise that you look into Ransomware Protection as soon as possible.
At One2call we can help you or your business with ransomware protection and it comes with a financially backed guarantee. Click on the link below to find out more about our financially backed ransomware protection so that you can be sure to be covered if the worst happens.
FREE Cyber Security Scans
Testimonials
Annette, Logo Leisurewear
Happy with excellent service by Pawel and Adam getting my new PC just as I need it to be set up. Thanks.
Peter, Peak Sensors
Very helpful, did exactly what I needed. Very competent people completing tasks accurately and quickly.
Cheryl, Chisholm UK
Jordan was very prompt and very helpful. All issues were resolved, or progressed further, right away.

